In today’s rapidly evolving cyber threat landscape, the traditional perimeter-based security model is insufficient. The rise of cloud services, remote work, and mobile devices has dissolved network boundaries, making Zero Trust an essential strategy. At its core, Zero Trust operates on the principle: never trust, always verify. Instead of assuming that entities within the network are safe, each user and device must continuously prove their legitimacy.
An identity-first Zero Trust approach places authentication and authorization at the heart of defenses. This means every access request—whether from an employee, contractor, or automated process—is validated against an identity policy before granting entry. Strong identity governance ensures that credentials, digital certificates, or biometric factors tie directly to the individual or device in question, reducing the risk of compromised access.
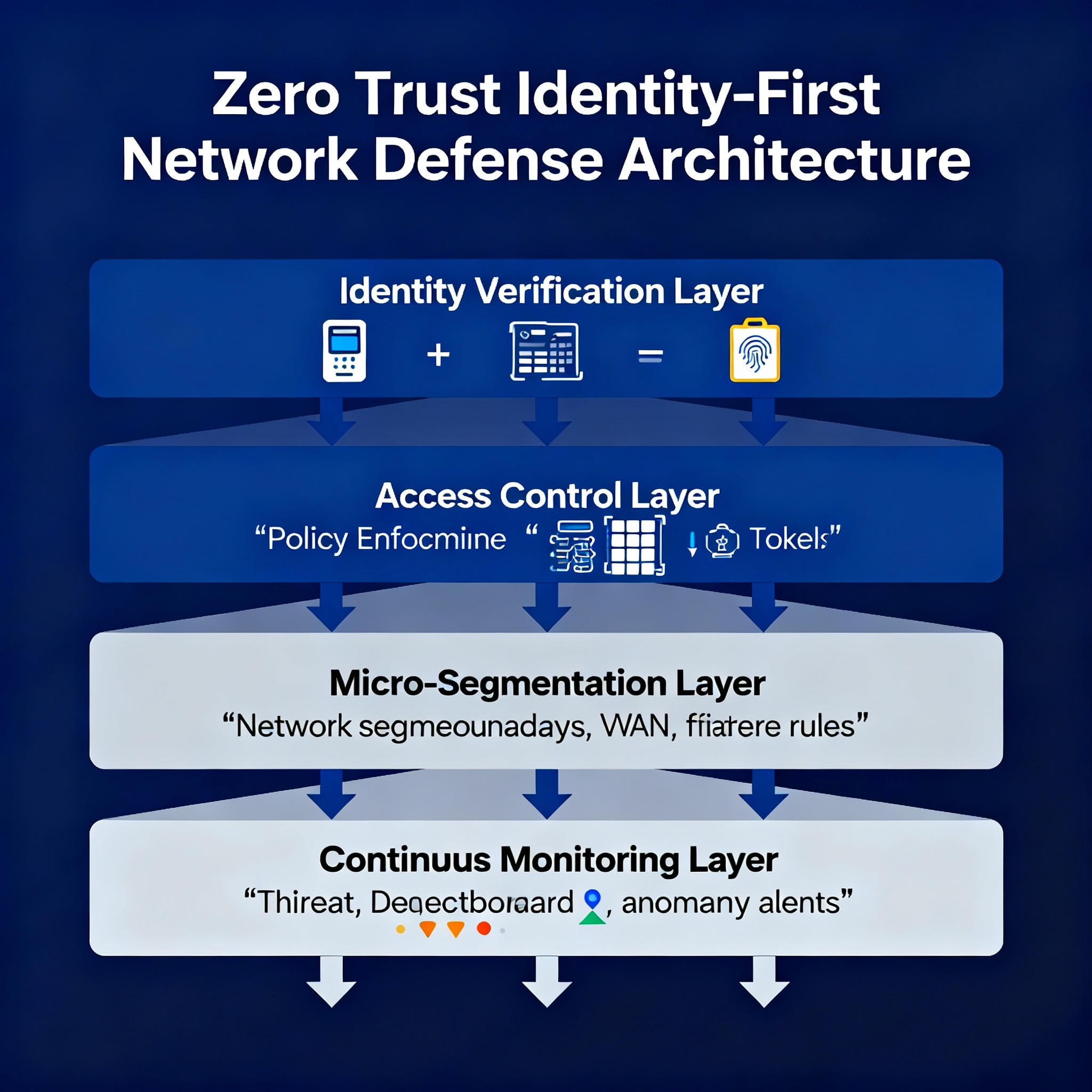
Core Principles of Identity-First Zero Trust
- Continuous Authentication: Move beyond one-time login. Use adaptive multi-factor authentication (MFA), passwordless technologies, and contextual risk scoring.
- Least Privilege Access: Grant the minimum permissions needed and revisit them regularly. Use role-based and attribute-based access controls (RBAC/ABAC).
- Segmentation and Microperimeters: Isolate sensitive data and applications, requiring separate authentication checkpoints.
- Real-Time Monitoring: Continuously inspect sessions for unusual patterns, such as data exfiltration attempts or inconsistent login behavior.
- Automated Response: Integrate security orchestration tools to revoke access instantly upon detecting irregularities.
Practical Steps for Implementation
- Map Identities Across the Environment: Inventory users, devices, API keys, and service accounts.
- Establish Strong Identity Providers (IdPs): Centralize authentication to trusted services like Okta, Azure AD, or Keycloak.
- Integrate Network and Identity Systems: Ensure your firewalls, VPNs, and SaaS platforms accept the same identity checks.
- Apply Conditional Access Policies: Block or limit logins based on geographic location, device health, or behavior patterns.
- Educate Users: Human error remains a vulnerability; train teams on phishing detection and secure credential handling.
When done correctly, identity-first Zero Trust transforms network defense into a dynamic, context-aware ecosystem. It reduces reliance on outdated perimeter models, tightly controls access to resources, and minimizes damage in case of a breach. As modern networks continue to evolve, identity will remain the most reliable anchor for enforcing trust and ensuring resilience against cyber threats.